Trust Infrastructure Core
These technologies form the civic backbone of the Autonomous Trust Infrastructure (ATI). They provide the enforcement logic that makes autonomy accountable, auditable, and safe.
.jpeg)
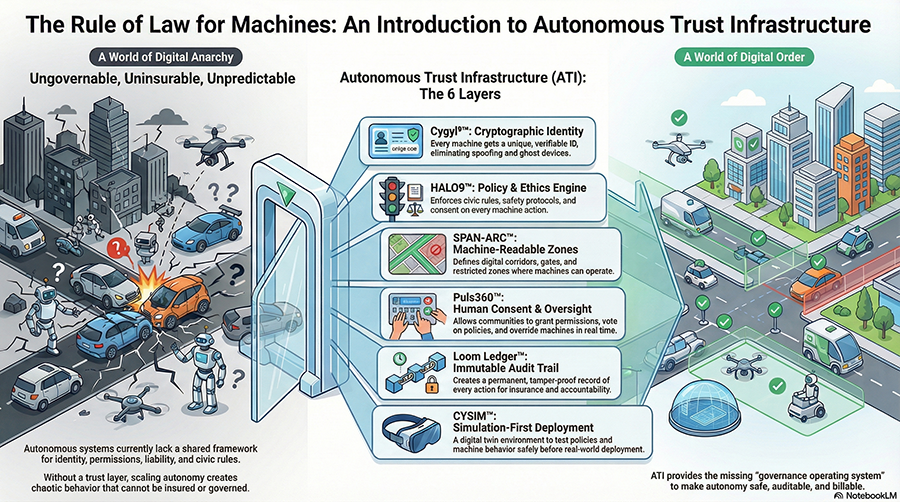
Cygyl⁹™ — Cryptographic Identity Ancho
Cygyl⁹ is the first line of defense in autonomy. It embeds a cryptographic ID into every Capsule, ensuring only verified agents can participate in trusted environments. It governs permissions, validates certificates, and revokes access in real time if rules are broken. Without Cygyl⁹, machines are anonymous; with it, they become accountable citizens of digital corridors.

HALO9™ — Contextual Behavior Engine
HALO9 acts as the conscience of autonomy. It continuously evaluates agent behavior against policy rules, ethics, and situational context. Whether it’s a drone crossing into a restricted zone or a scooter drawing power from a charging pad, HALO9 decides if the action is permitted, denied, or requires human oversight.

Nucleus7™ — Trusted Execution Kernel
Nucleus7 is the “circuit breaker” inside the ATI Stack. It enforces safe execution boundaries at the hardware and firmware levels, stopping unauthorized code from running and ensuring compliance with corridor policies. It’s designed for zero-trust environments where every instruction must be verified.

Loom™ — Decentralized Orchestration System
Loom is the coordination fabric. It connects Capsules, Gates, Corridors, and Policies into a living network of trust. When an agent requests entry, Loom consults the rules, gathers consent tokens, and orchestrates the decision. Loom transforms fragmented autonomy into a governed civic ecosystem.

Loom Ledger™ — Immutable Audit Trail
Loom Ledger is where trust becomes provable. Every event — an agent entering a gate, a consent override, or a policy enforcement — is recorded on an immutable ledger. Communities, regulators, and insurers can audit these logs to verify compliance, resolve disputes, or replay incidents. Loom Ledger makes autonomy transparent.

.jpeg)








